Active Directory Deception
WHY IS MY AD AT RISK?
The most efficient way for a hacker to gain access to a corporate network is to hack an administrator account. Where? In an Active Directory. To locate them, attackers use sophisticated tools.
How can I protect my Active Directory?
When CYBERTRAP Active Directory Deception is active, it detects any scan for privileged user accounts and uses this opportunity to send the hacker false credentials. As soon as the attacker uses these to navigate further in the network, he falls into the trap.
The intruder is undetectably redirected to a deceptively real Active Directory image, the Deception environment. There, he can “let off steam” without causing any harm or finding any genuine company data. At the same time, by precisely monitoring the attack and analyzing the attack tactics, the company’s own Active Directory is strengthened against future attacks.
This is why you should choose CyberTrap
CyberTrap does not affect your operations or the live system
CyberTrap is ready for use within one day
CyberTrap is invisible to attackers and employees
Benefit from attack information in real time
For whom is Active Directory Deception suitable?
You can invest in the protection of your company’s assets in many ways. Unfortunately, there is no such thing as guaranteed lifetime security for living systems such as IT infrastructure. A breach (possibly still undiscovered) will always be found, or new vulnerabilities will emerge, for example as a result of updates. Another contributing factor is a lack of patch management or so-called phishing attacks, in which attackers use fake emails or telephone calls to obtain an employee’s access data directly.
It is less a question of company size than the willingness or need to take advantage of the latest technology. Even large IT system companies can benefit from the added credibility a CyberTrap partnership brings, giving them an edge in the marketplace.

Need clarification?
Why are Active Directories particularly vulnerable?
For attackers, Active Directory is an ideal hiding spot from security teams and their standard tools. Once they infiltrate the system, hackers utilize specialized tools to map out the entire Active Directory environment. This allows them to pinpoint valuable resources, critical systems, and privileged user accounts that they can exploit to their benefit.
Why are Active Directories popular points of attack?
Active Directories are popular points of attack because they are widely used by organizations to manage user and computer access to corporate resources. Every computer on the corporate network must have access to Active Directory for the network environment to function properly, making it a central point of control. This widespread reliance simplifies a hacker's job, as gaining access to Active Directory can provide extensive control over the entire network and its resources.
Why do hackers find Active Directory admin accounts so interesting?
Hackers find Active Directory admin accounts particularly interesting because administrators usually have extended privileges that allow them to create and configure domains, retrieve data, and access protected areas. By misusing existing credentials, such as an admin account, hackers can gain extensive control over the network and remain undetected for a long time, making it easier to exploit the system and access valuable resources.
What techniques and tools do hackers use to look for administrator accounts in an Active Directory?
Hackers use a variety of techniques and tools to look for administrator accounts in an Active Directory. Here are some common methods:
Techniques
- Reconnaissance and Enumeration
- LDAP Queries: Hackers use Lightweight Directory Access Protocol (LDAP) queries to gather information about the directory structure, user accounts, and group memberships.
- Net Commands: Using commands like net user and net group, attackers can list user accounts and their group memberships.
- Password Spraying
- This technique involves trying a few common passwords against many accounts to avoid account lockouts and detect weak passwords.
- Credential Dumping
- Hackers dump credentials from memory or local storage using tools like Mimikatz to obtain hashed or clear-text passwords of administrator accounts.
- Pass-the-Hash and Pass-the-Ticket Attacks
- Using hashed passwords (NTLM hashes) or Kerberos tickets obtained from compromised accounts to authenticate as administrators without knowing the actual password.
- Privilege Escalation
- Exploiting vulnerabilities or misconfigurations to escalate privileges from a lower-level account to an administrator account.
Tools
- Mimikatz
- A powerful tool used to extract plaintext passwords, hashes, PIN codes, and Kerberos tickets from memory.
- BloodHound
- An Active Directory (AD) enumeration tool that maps out relationships and privileges, helping attackers identify paths to escalate privileges.
- PowerView
- A PowerShell tool that aids in gathering information about the AD environment, including users, groups, and permissions.
- Responder
- A tool used to capture credentials by tricking systems into authenticating against a rogue server controlled by the attacker.
- Metasploit
- A penetration testing framework that includes various modules for Active Directory attacks, including enumeration and credential dumping.
- Kerbrute
- A tool used for brute-forcing and enumerating valid Active Directory user accounts through Kerberos Pre-Authentication.
- SharpHound
- A data collector used by BloodHound to gather information about the Active Directory environment for analysis.
- CrackMapExec
- A post-exploitation tool that helps in network reconnaissance and exploitation of Active Directory environments.
By using these techniques and tools, hackers can effectively search for and exploit administrator accounts within an Active Directory environment, often remaining undetected for long periods.
How is an attacker redirected into the Deception environment?
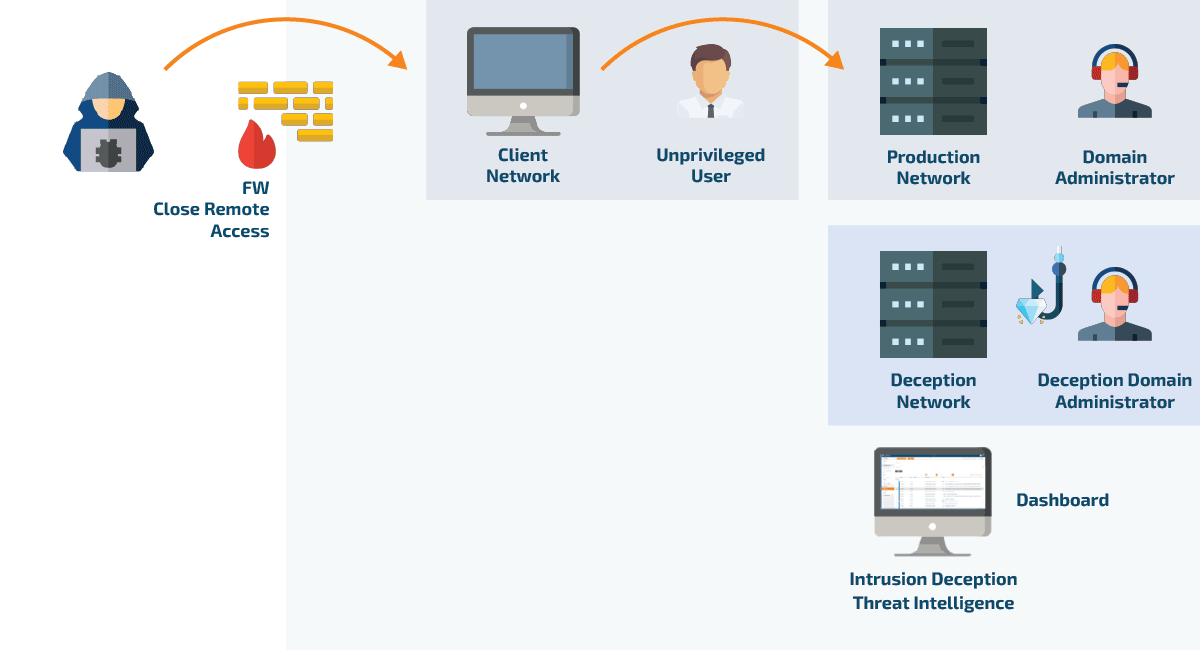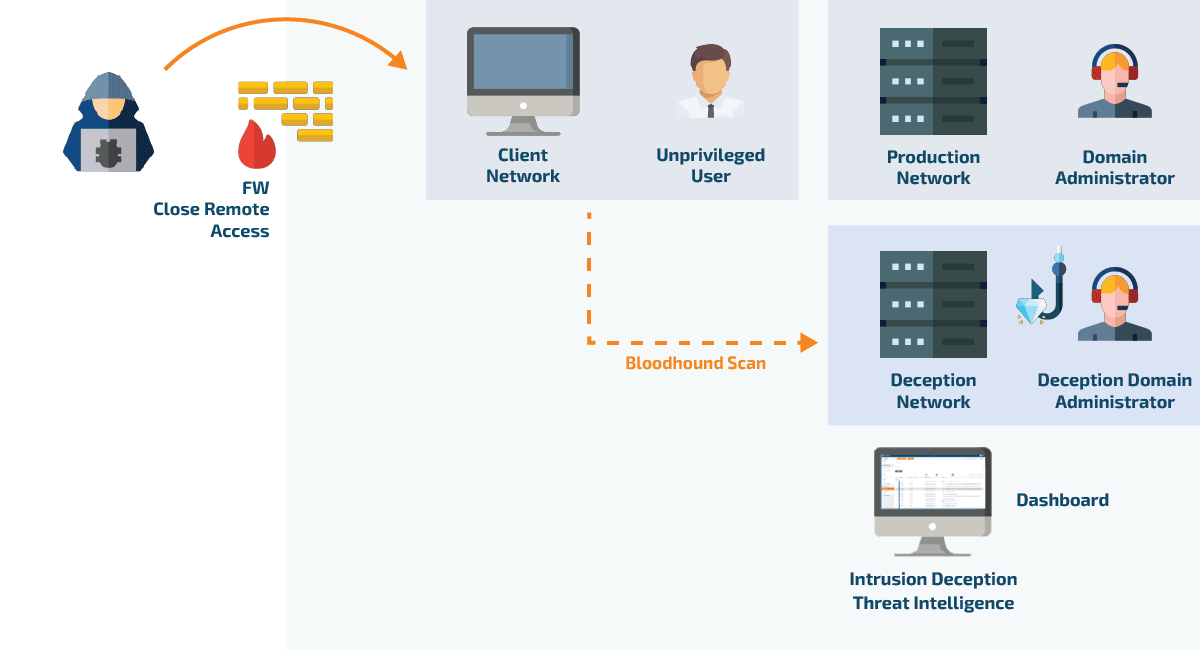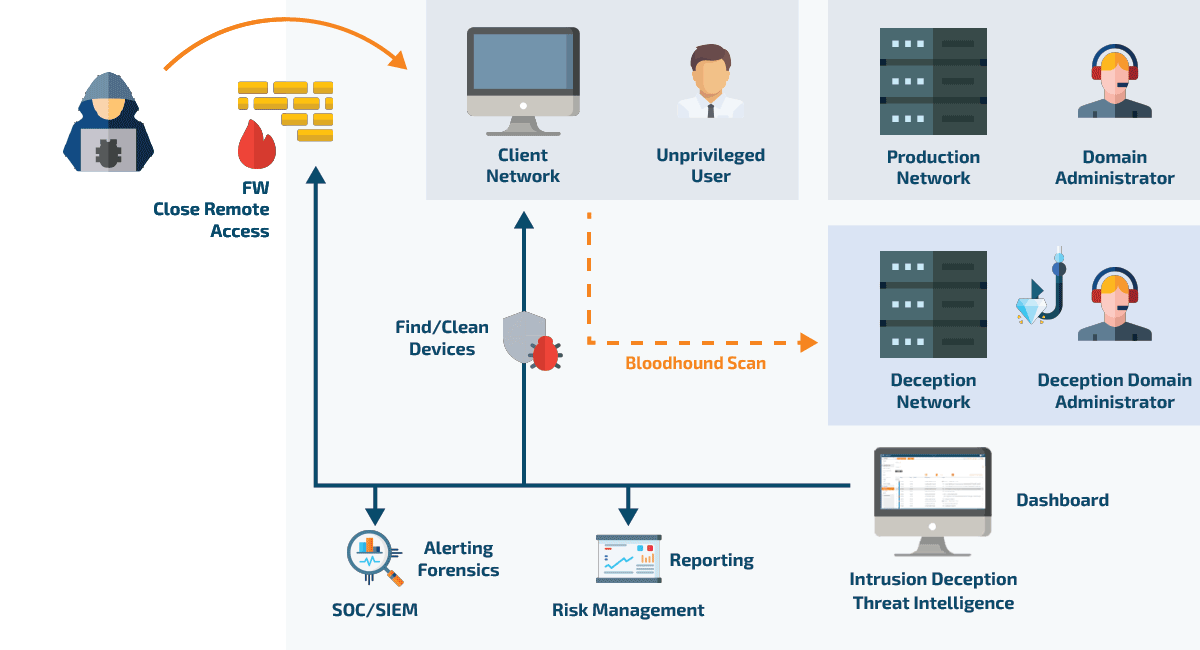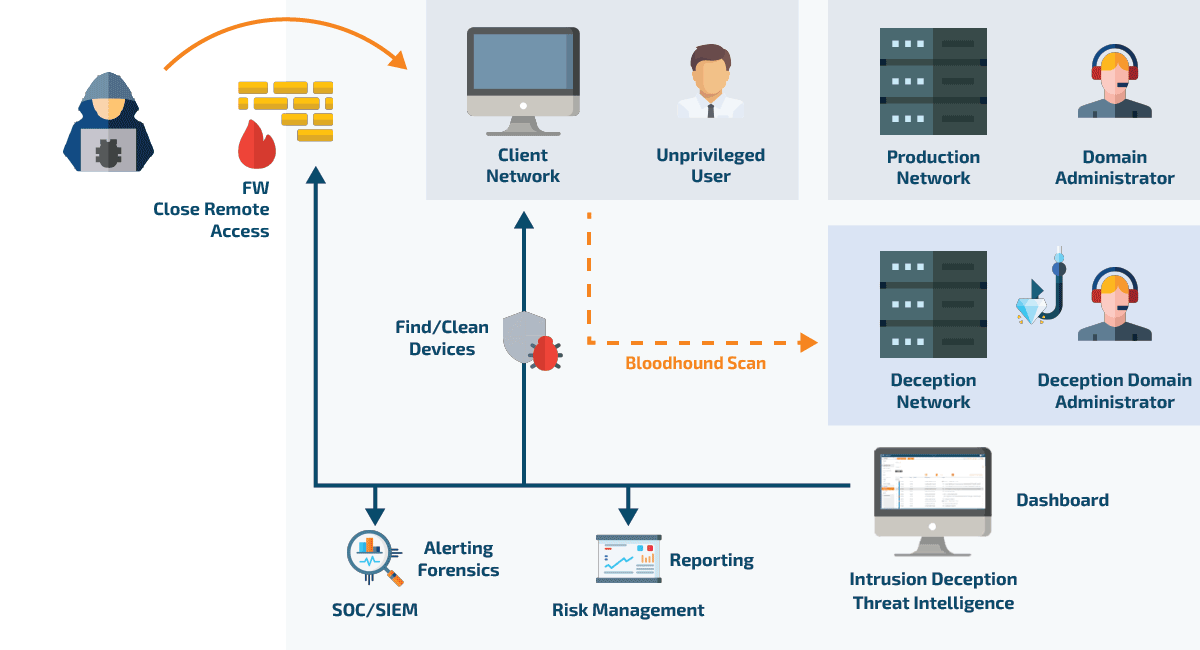
When CyberTrap Active Directory Deception is active, attackers are cleverly redirected into a deception environment through the use of fake credentials. Here's how it works:
When a hacker scans the network for admin accounts, they receive fake credentials specifically designed to appear legitimate. Once the attacker uses these fake credentials, they are automatically redirected into a meticulously crafted replica of the corporate network, known as the deception environment. This environment mimics the real network, ensuring the attacker is unaware of the switch.
Within this deception environment, the attacker can interact with what they believe are genuine systems and data, allowing them to continue their activities undetected. Meanwhile, the IT administrator in charge is immediately notified of the attack. This setup not only isolates the attacker, preventing any real damage to the actual network, but also allows for the monitoring and analysis of the attacker's behavior, providing valuable threat intelligence.
Why doesn’t the attacker realize they are getting false credentials?
The credentials that the attacker receives are intended for actual systems with real operating systems and services, the so-called traps (decoys). These decoys are meticulously designed to be indistinguishable from legitimate systems within the corporate network.
As a result, the attacker cannot determine whether these credentials are real or fake because they do not differ in any way from genuine credentials. The decoys respond as real systems would, providing the attacker with a seamless and convincing experience. This meticulous replication ensures that the attacker remains unaware of the deception, allowing them to proceed with their activities as if they were interacting with actual network assets.