Web Application Deception
Why Are Web Applications at Risk?
Even if you regularly update your Web Applications and implement effective patch management for third-party software, there is no such thing as guaranteed full protection. The security of the entire infrastructure will always depend on the weakest element in your network. Constantly checking third-party libraries used in programming not only requires the necessary IT know-how but also costs a lot of time.
Experience shows that hackers often find vulnerabilities faster than they are patched by manufacturers. Weak passwords or phishing attacks, in which the attackers get hold of an employee’s access data directly via fake emails or telephone calls, also play a part.
How Can I Protect My Company’s Web Applications?
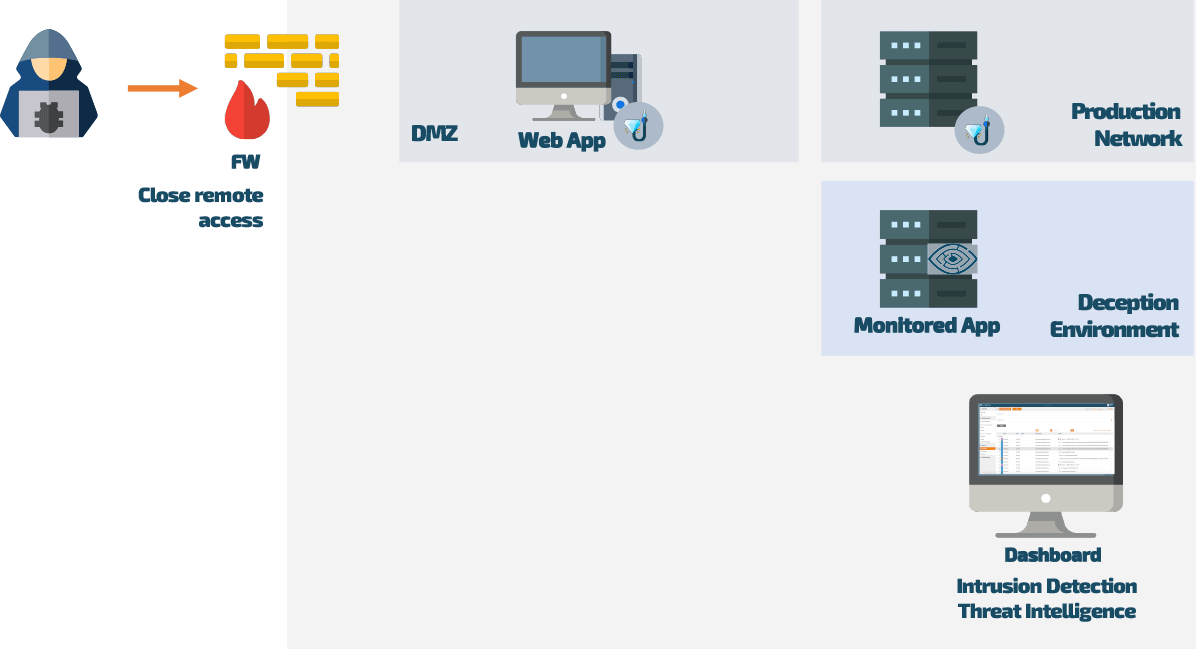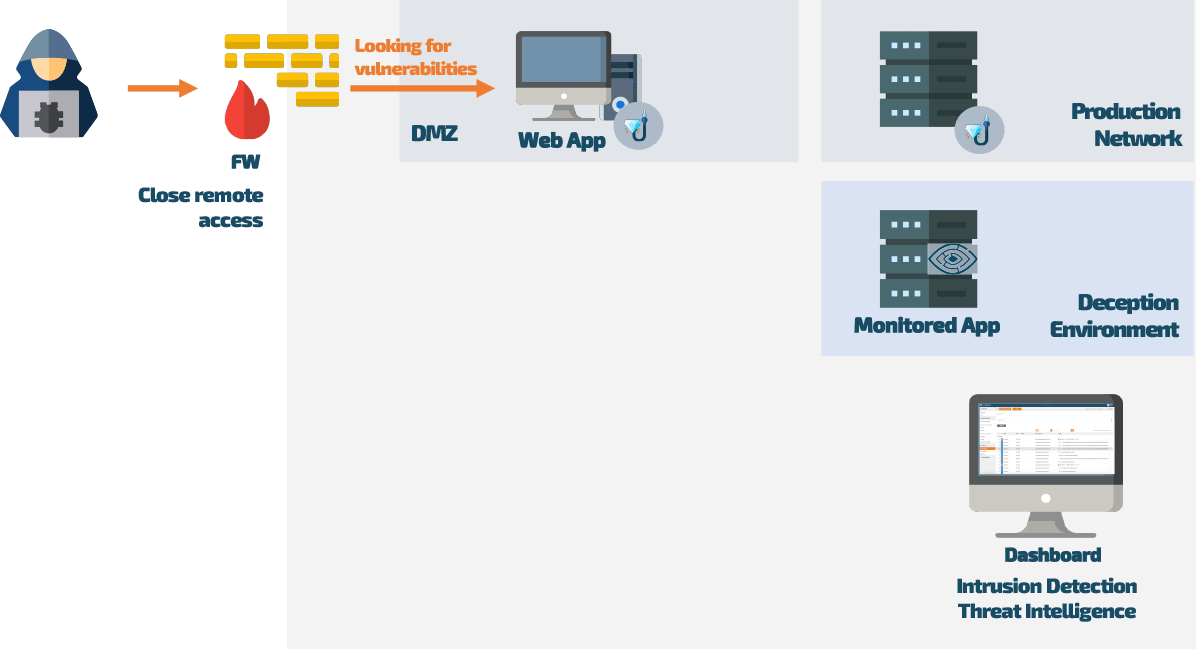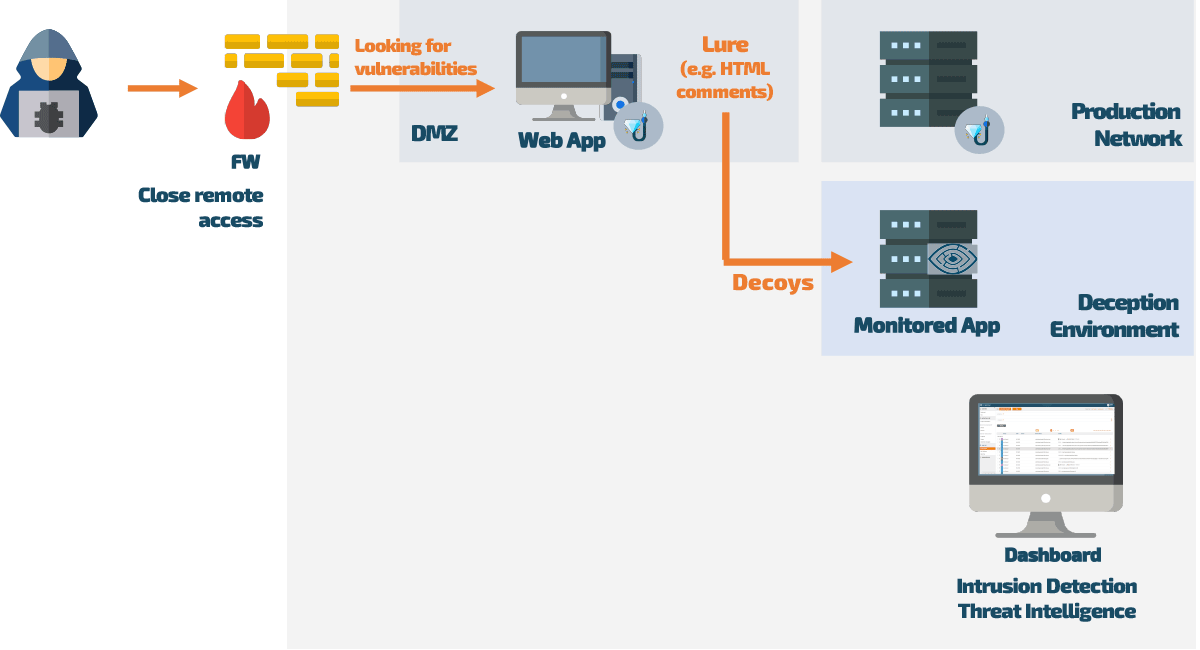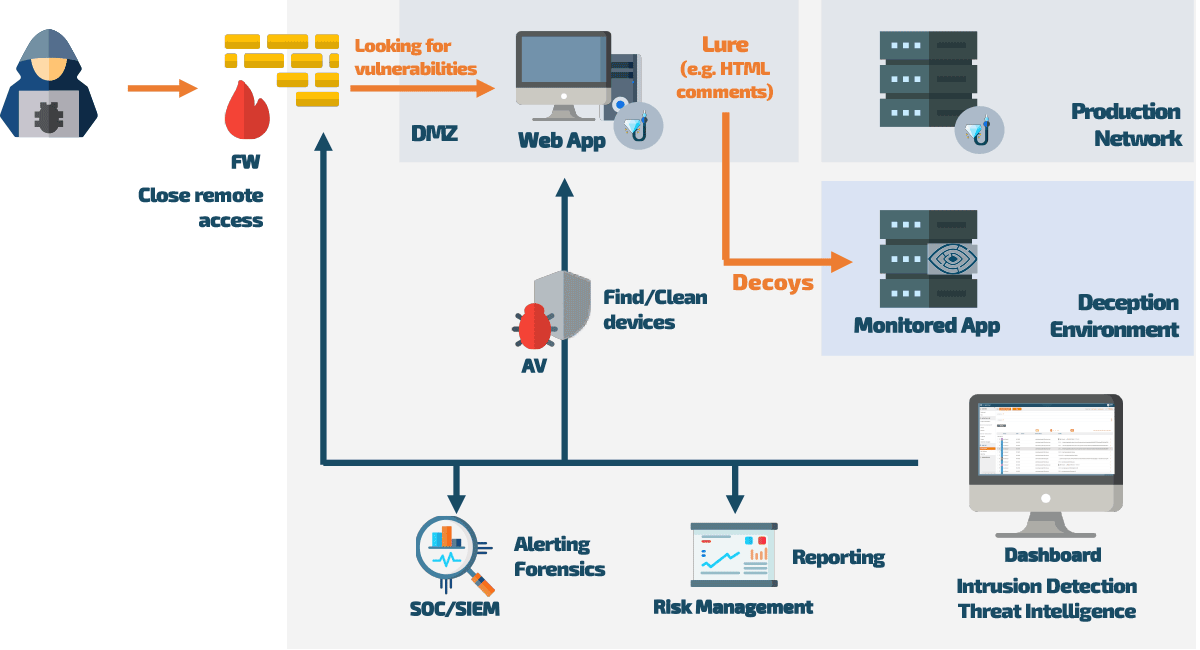
To successfully prevent a hacker attack with Web Application Deception, an older version of the application is specially prepared and placed online. To potential attackers, everything looks so real that they inevitably stumble upon strategically placed lures in the application’s source code. These lures (invisible to normal users) are directly linked to monitored traps called decoys. As soon as a hacker follows one of the lures, they are tracked at every turn.
In the Web Application Deception environment, the uninvited guest can “let off steam” without causing any harm or finding any genuine company data. At the same time, the system monitors and evaluates the behavior of the attacker, generating valuable threat intelligence data that can be accessed via a dashboard or risk management reports. This data can be imported into any SOC/SIEM systems, anti-virus software, and firewalls to holistically strengthen security measures in the production network.
This is why you should choose CyberTrap
CyberTrap does not affect your operations or the live system
CyberTrap is ready for use within one day
CyberTrap is invisible to attackers and employees
Benefit from attack information in real time
Who Can Benefit from Web Application Deception?
CyberTrap Web Application Deception is ideal for businesses, critical infrastructure providers, banks, and government agencies that are either facing targeted hacker attacks or have already fallen victim to them. This advanced security solution is tailored to meet the needs of organizations that require robust protection against sophisticated threats.
By deploying Web Application Deception, these entities can effectively detect, divert, and analyze malicious activities, ensuring the integrity and security of their critical data and systems. Whether you are dealing with persistent threats or looking to fortify your defenses, CyberTrap provides the necessary tools to stay ahead of cyber adversaries.

Need clarification?
Why are corporate Web Applications a popular point of attack for hackers?
Corporate web applications are often targeted by hackers because they are frequently not well-programmed or thoroughly tested, leading to vulnerabilities that can be easily found and exploited.
Which Web Applications can be protected with Deception technology?
Any application, internal or accessible from the Internet can be enhanced and protected by Deception technology.
Why are Web Applications a popular point of attack?
Web applications are popular targets because they often lack adequate testing, making them susceptible to vulnerabilities that hackers can exploit.
Which Web Applications are particularly vulnerable?
Every application on the Internet is vulnerable, especially if users can log in and retrieve services or data. Thus, the website of a public institution could be as interesting to hackers as online banking, a webshop, or a fundraising site for a non-profit organization.
Which vulnerabilities are particularly interesting for hackers?
Error pages, entries in robots.txt, interesting subdomains, and similar elements are particularly intriguing for attackers. Although these elements are not visible to users visiting the application with a browser (and are therefore often overlooked during testing), they are easily visible to hackers and their tools.
How is an attacker redirected into the Deception environment?
When Web Application Deception is active, the web application is loaded with special lures that are indistinguishable from the actual application to the hacker. Once redirected to the decoys, the attacker can no longer cause any damage to the actual application, and the responsible IT system administrator is notified via an alert.