Endpoint Deception
WHY ARE ENDPOINTS PARTICULARLY AT RISK?
Corporate networks generally consist of more than just computers. Webcams, printers, WLAN routers, and a lot of other IoT devices are also indispensable in offices, production facilities, and even critical infrastructure. So, if just one of these endpoints in the network is hacked, for example through vulnerabilities in the firmware, the entire corporate infrastructure is compromised.
How can I protect end devices on the network?
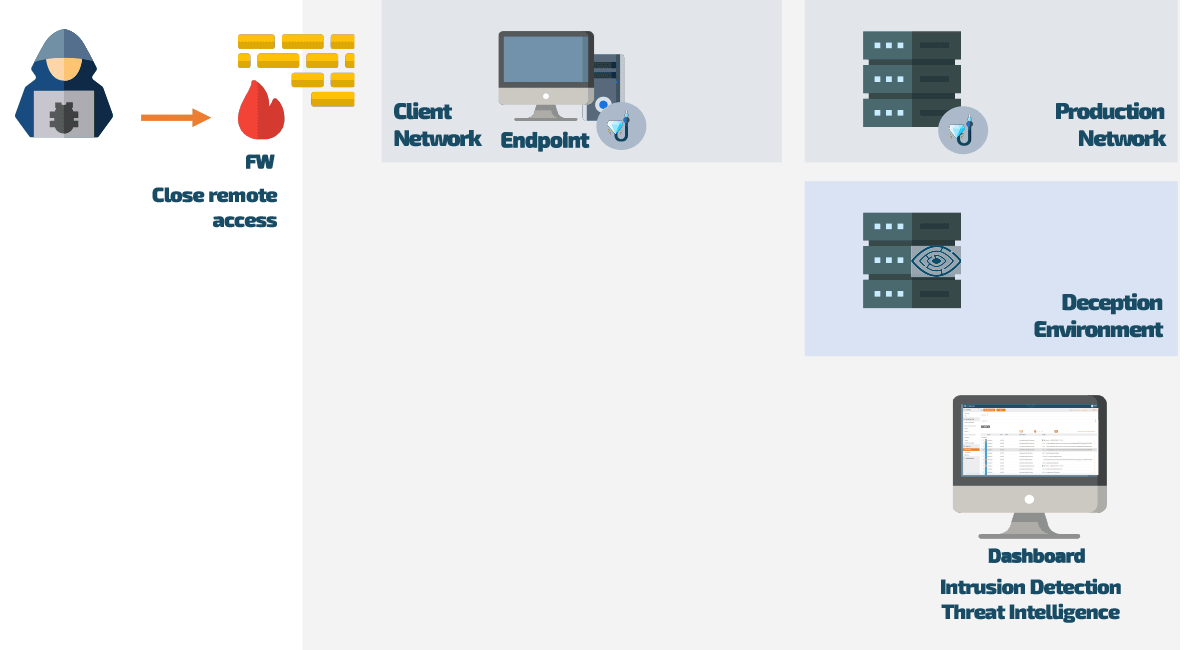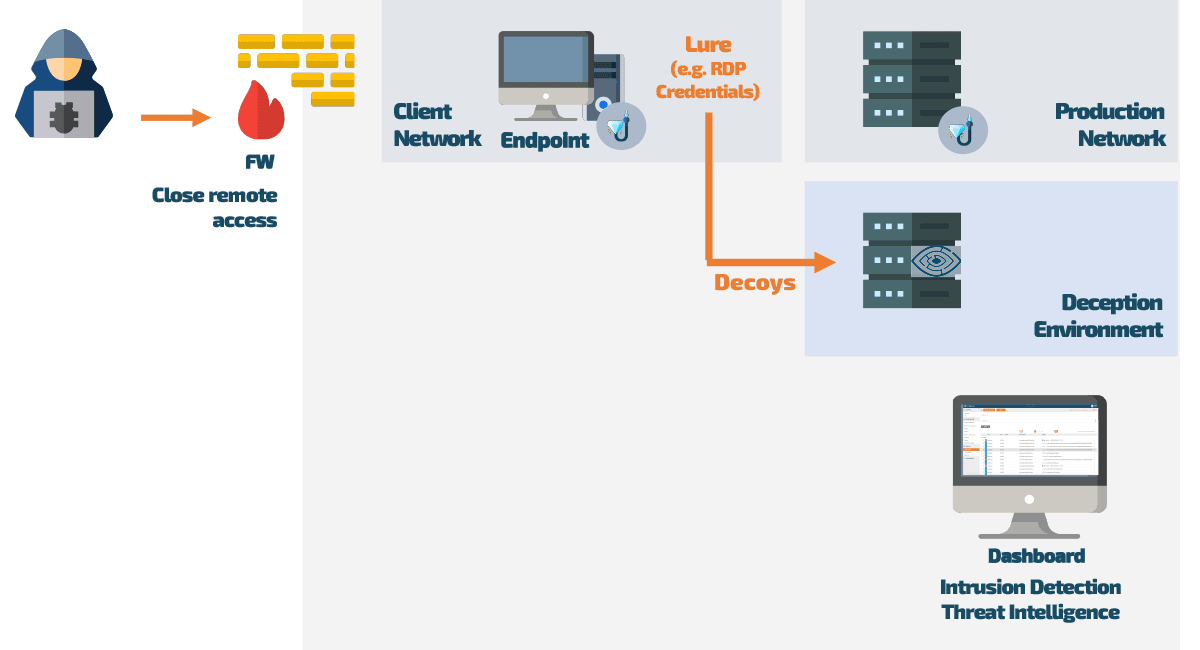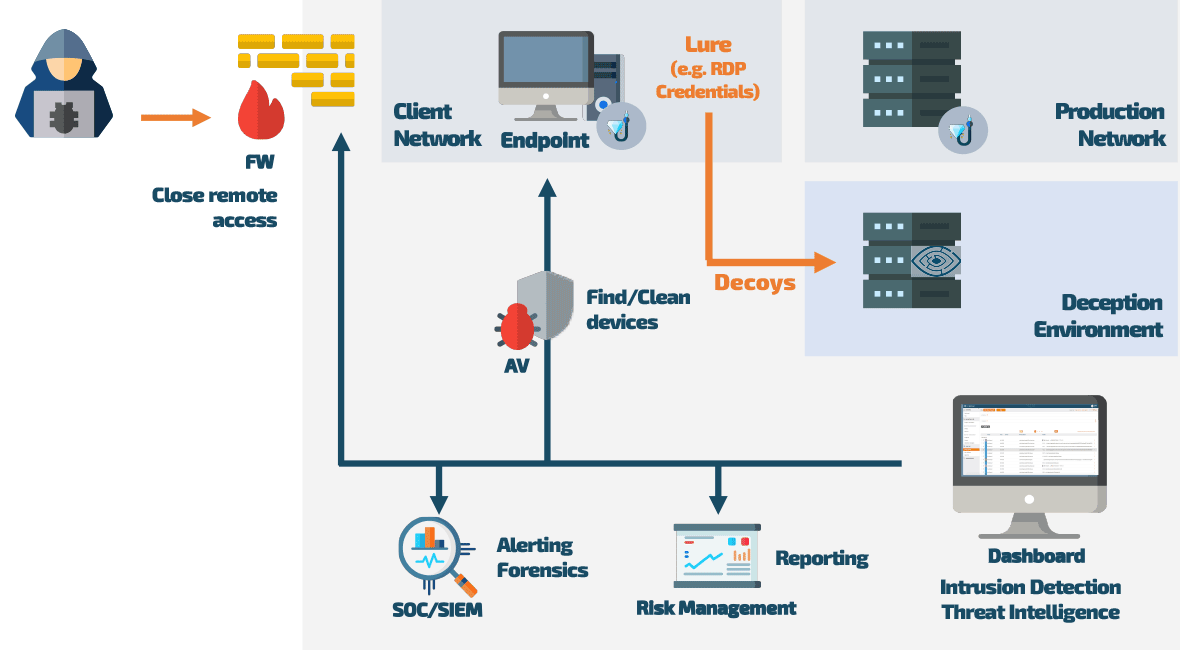
Once CyberTrap Endpoint Deception is rolled out on the network, hidden lures are deployed on the endpoints. These lures are designed and customized specifically for your network so that an attacker cannot differentiate them from the actual network elements.
By using these lures, the intruder is thus undetectably redirected to a deceptively real image of the productive network, the decoys in the deception environment. There, he can “let off steam” without causing any harm to production systems or finding any genuine company data.
At the same time, the decoy monitors and evaluates the behavior of the attacker, generating valuable threat intelligence data that can be accessed via a dashboard. This data can be exported into any SOC/SIEM system, and combined with anti-virus, or firewall logs to give a holistic overview of what is currently happening.
This is why you should choose CyberTrap
CyberTrap does not affect your operations or the live system
CyberTrap is ready for use within one day
CyberTrap is invisible to attackers and employees
Benefit from attack information in real time
Do you need Endpoint Detection?
Even if you regularly update your Software Applications and implement effective patch management for third-party software, there is no such thing as guaranteed full protection. The security of the entire infrastructure will always depend on the weakest element in your network. Experience shows that hackers often find vulnerabilities faster than they are patched by manufacturers.
A breach (possibly still undiscovered) will always be found, or new vulnerabilities will emerge, for example as a result of updates. Phishing attacks, in which the attackers get hold of an employee’s access data directly via fake emails or telephone calls, also play a part.
It is less a question of company size than the willingness or need to take advantage of the latest technology. Even IT security companies can benefit from the added credibility a CyberTrap partnership brings, giving them an edge in the marketplace. The threat intelligence information generated by CyberTrap Endpoint Deception, provided in real-time and in MITRE/ATT@CK context, helps the SOC team to focus on critical alerts and analyze them more effectively.

Need clarification?
Why are endpoints on the network vulnerable?
Every endpoint in a production network is a potential entry point for a hacker. Once on the network, the attacker can use their specialized hacking tools to move on undetected and elevate their privileges, all the way up to administrator. Research shows that attackers can remain on the network for up to several months before conventional security systems detect them.
Which endpoints are most interesting to hackers?
The most interesting endpoints for hackers are those that are poorly monitored or on which the latest software is not or cannot always be installed immediately. They serve as a simple gateway for hackers to navigate their way around the network undisturbed.
Why are IoT devices a popular point of attack?
The basic software of IoT devices is a so-called firmware. It is comparable to the operating systems of computers and servers. In many cases, this firmware is obsolete or is not updated as often, and thus the risk that it presents a vulnerability that an attacker can exploit is significantly higher than with conventional operating systems.
How is an attacker redirected into the Deception environment?
When our Endpoint Deception is active, a hacker will find deliberately placed but false information as he searches the network. As a result of using this false information, this attacker automatically ends up in a perfect replica of the corporate network (the Deception environment) at which point the responsible IT system administrator gets notified via an alert.
Why doesn’t the attacker realize that he is getting false credentials?
The credentials that the attacker receives are intended for actual systems with real operating systems and services, the so-called traps (decoys). Therefore, he can never determine whether these credentials are real or fake because they do not differ in any way from real credentials.
How long do hackers without deception technology remain undetected on the network?
The global average of the so-called “dwell time” was recently estimated at 56 days. With CyberTrap Endpoint Deception you can reduce the dwell time of otherwise undetected attackers in your network by up to 97%.