Deception Technology
What your organization needs to protect your business against increasingly sophisticated attacks.
Deception Technology works by deliberately diverting attackers into a specially created IT environments
even before they can penetrate further into the company’s actual infrastructure
Within this fictitious environment, it is possible to systematically observe the attackers to
identify their motivation, methods, and in some cases, even their identity and clients
How Hackers Operate
During the first stage of the cyber attack, also known as the Reconnaissance phase, hackers observe and examine the structure of the network and the layout of hierarchies.
Hackers use various tools to expose vulnerabilities or paths to reach the desired location in the network.
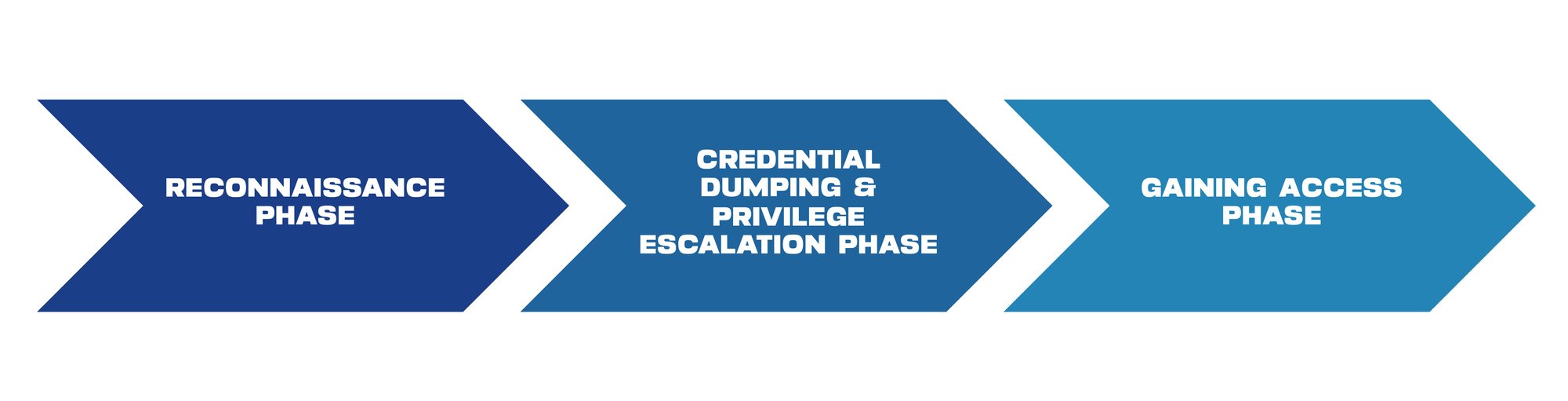
After the intrusion, in the Credential Dumping and Privilege Escalation phase, hackers move through the network step by step in order to gain greater user rights and thus reach the target of his attack.
If they have managed to gain admin rights, they move into the Gaining Access phase, and it becomes even more difficult to identify lateral movements between devices and apps, as it looks like normal network traffic.
Attackers invariably use deception techniques, so why shouldn’t defenders?

Ever-Evolving Cyber Threats
In the landscape of ever-evolving cyber threats, artifacts such as logs, timestamps, and registry entries serve as crucial forensic evidence of potential intrusions into a network. These artifacts provide a historical record of activity that can be analyzed to identify breaches and understand attacker behavior.
However, the nature of this information is inherently dynamic, as it is based on data that is constantly being gathered and updated. Attackers are continuously refining and altering their techniques, tactics, and procedures (TTPs), which means that the evidence left behind can vary significantly over time.
This ongoing evolution requires security measures and forensic analysis techniques to be equally adaptive, ensuring they can effectively identify and respond to new forms of threats as they emerge.
No, honeypots are not enough!
IT security is an ongoing responsibility and should not be viewed as a one-time investment. The field is constantly evolving.
Hackers are continuously finding new ways to break into systems or exploit emerging security vulnerabilities.
Just as you take a car in for regular service, occasionally buying new tires or replacing worn parts, IT systems and especially cybersecurity components require continuous improvments.
Honeypots were originally designed to detect hacker activities. However, adversaries no longer fall for these.
Today, the goal is to deceive hackers, wasting their time and resources while remaining as inconspicuous as possible. Only modern deception solutions can achieve this.

Deception Tactics Protect Data
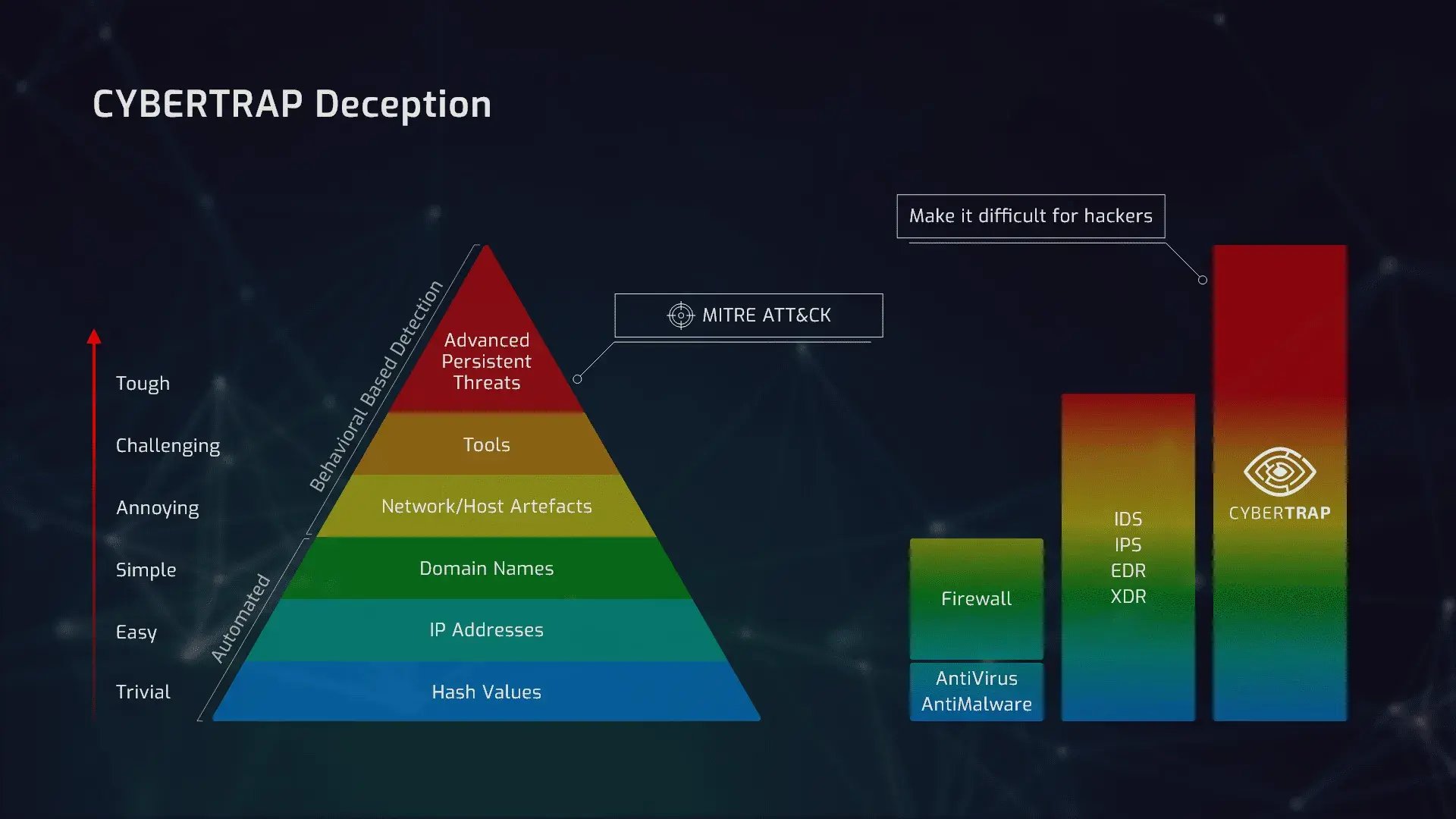
The extent (or lack thereof) to which popular hardware and software in IT security are actually used to defend against attackers is well illustrated in the so-called “Pyramid of an Attackers Pain” (David J Bianco, Mandiant/Fireeye).
It shows that the challenge for hackers increases from the bottom, lower layers, such as anti-malware and firewall systems, to the top.
At the top of the list is the MITRE ATT&CK Framework®, designed to better identify attacker behavior in the event of a breach. To learn more about how our deception technology maps to this framework, and what recommendations it provides, read the article on Deception Stories.
3 STEPS TOWARDS BETTER SECURITY
Schedule deployment
It only takes a few hours until the solution is ready for use. You schedule the most convenient time with our technical department.
You then decide whether your IT department should take care of the ongoing support or whether to outsource this task to us until the appropriate know-how is available internally.
WHICH DECEPTION SOLUTION IS RIGHT FOR MY BUSINESS?
We currently offer three different solutions for your deception campaigns. Each of them can be managed by your technical team. If you choose to outsource this part our knowledgable resellers and distributions are happy to help.
State-of-the-art security technology is particularly suitable for banking, finance, pharmaceutical and industrial companies. But even SMEs, which often lack IT expertise altogether, find themselves increasingly at the mercy of the growing number of hacker attacks. Unfortunately, so-called herd immunity does not work against targeted or random attacks.
Endpoint Deception
Even if specific devices on the network are compromised, the rest of the infrastructure is protected. The decoys are custom-designed and tailored for your network so that an attacker cannot differentiate them from the actual network elements.
Once trapped on the decoy there is no way back to the production network.
Active Directory Deception
By gaining access to an Active Directory, attackers aim to hide from security teams and their tools. Unknowingly, they obtain fake credentials.
Unnoticed, scan the entire Active Directory and search for admin users. Our solution sends back such data, detects the attack and thus redirects the attackers.
Web Application Deception
We place autonomous lures at strategic positions of your web applications. These lures refer to a deceptive trap system (decoy), on which the attacker can run riot and do no harm.
In the process, a digital profile of the attacker is created and made available to other systems.
Deception technology at a glance
What is Deception Technology?
Deception technology is an innovative approach in the cybersecurity landscape designed to detect, divert, and analyze cyber threats. Unlike traditional security measures, which primarily focus on perimeter defenses, deception technology strategically plants decoys and lures within the network to mislead and trap attackers. This proactive approach not only identifies malicious activities but also provides deep insights into the attackers’ tactics, techniques, and procedures (TTPs).
How Deception Technology Works
Deception technology operates by deploying realistic decoys and lures throughout a network. These decoys mimic genuine network assets such as servers, applications, and data, creating a highly believable environment for attackers to interact with. When an attacker engages with these decoys, the system generates alerts that enable security teams to respond quickly and effectively. The decoys are designed to appear as real as possible, making it difficult for attackers to distinguish between genuine assets and deceptive elements.
Benefits of Deception Technology
Early Detection of Threats
Deception technology excels at identifying threats early in the attack lifecycle. By interacting with decoys, attackers inadvertently reveal their presence, allowing security teams to detect and respond to threats before they can cause significant damage. This early detection is crucial in preventing data breaches and minimizing potential losses.
Reduced False Positives
Traditional security measures often suffer from high false positive rates, which can overwhelm security teams and lead to alert fatigue. Deception technology, by contrast, generates alerts only when an attacker interacts with a decoy, ensuring that alerts are accurate and actionable. This reduction in false positives helps security teams focus on genuine threats and respond more efficiently.
Detailed Threat Intelligence
Interacting with decoys allows security teams to gather valuable threat intelligence. Analyzing attackers' actions within the deception environment provides insights into their methodologies and goals. This intelligence is crucial for understanding emerging threats and improving overall security posture. By learning how attackers operate, organizations can develop more effective defensive strategies and anticipate future attacks.
Disruption of Attackers’ Activities
Deception technology effectively disrupts attackers' activities by diverting them away from actual network assets. Engaging with decoys wastes attackers’ time and resources, reducing their chances of successfully compromising critical systems. This disruption is a key advantage, as it not only protects valuable data but also frustrates and demoralizes attackers.
Integration with Existing Security Solutions
Deception technology can seamlessly integrate with other security solutions such as Security Information and Event Management (SIEM) systems, Endpoint Detection and Response (EDR) tools, and firewalls. This integration enhances the overall effectiveness of the security infrastructure, allowing for comprehensive threat detection and response.
CyberTrap's Advanced Deception Technology
CyberTrap offers a cutting-edge deception technology solution that sets itself apart in the cybersecurity market. Here’s how CyberTrap’s solution stands out:
Comprehensive Threat Analysis
CyberTrap provides the most detailed analysis of TTPs and attacker objectives among leading deception solutions. Its built-in analyzer assists security engineers by offering deep insights into attacker behavior, helping organizations stay ahead of evolving threats. This comprehensive analysis is critical for developing robust defensive measures and improving overall cybersecurity strategies.
Flexible Deployment Options
CyberTrap supports on-premise, hybrid, and cloud-based deployments, making it the most versatile solution available. Decoys can be strategically placed anywhere within the customer’s network, enhancing the overall security posture. This flexibility ensures that CyberTrap can meet the unique needs of any organization, regardless of its infrastructure.
Agentless Operation
Unlike many deception solutions that require endpoint agents, CyberTrap operates without agents on endpoints. This agentless approach ensures reliability and eliminates the risks associated with endpoint agent updates and failures, as seen with recent issues from other security solutions. CyberTrap’s fully automatic lure installation via a small self-destructing installer makes it undetectable and reliable.
High Interaction Decoys
CyberTrap’s decoys are highly interactive and closely mimic real systems, effectively engaging attackers. Regular systems are transformed into decoys by installing CyberTrap’s monitoring component, a Microsoft-certified Kernel component that allows for fine-grained monitoring. This high level of interaction provides a realistic environment for attackers, making it easier to gather valuable threat intelligence.
Seamless Integration
CyberTrap integrates smoothly with other security solutions via syslog and CyberTRAP’s API. This interoperability ensures that CyberTrap can enhance existing security frameworks, providing a robust defense against sophisticated cyber threats. Integration with SIEM and SOAR systems allows for comprehensive threat management and streamlined incident response.
Enhanced Monitoring and Threat Intelligence
CyberTrap’s decoys monitor and evaluate attacker behavior in real-time, generating valuable threat intelligence data. This data can be accessed via a centralized dashboard and integrated into SOC/SIEM systems, antivirus software, and firewalls, providing a holistic view of the security landscape. By continuously monitoring attacker activities, CyberTrap helps organizations stay informed about emerging threats and adapt their defenses accordingly.
Resilient Infrastructure
CyberTrap’s architecture is designed for high availability and resilience. The decoys and monitoring components are robust and can be strategically deployed across different network segments, ensuring continuous protection and minimal disruption. This resilient infrastructure is essential for maintaining a strong security posture and preventing potential breaches.
In a nutshell
Deception technology is a powerful tool in modern cybersecurity, offering early detection, reduced false positives, detailed threat intelligence, and effective disruption of attackers’ activities. CyberTrap’s advanced deception technology stands out for its comprehensive analysis, flexible deployment options, agentless operation, and seamless integration, making it a leading choice for organizations seeking to enhance their cybersecurity defenses. By deploying CyberTrap, organizations can stay one step ahead of cyber adversaries, protect their critical assets, and maintain the integrity of their networks.