Test your hacking skills at it-sa 2021 in Nuremberg and experience Cybertrap Deception technology live.
Do you have what it takes to be a hacker?
In a world that is becoming increasingly digital, we have come up with something special for this year’s it-sa trade fair and are building a playground for hackers. Test your skills at several brain-bending stations such as the Wobble Tower, the Climbing Path and the Hot Wire. Just as hackers want to move around the network as inconspicuously as possible, your mission is to get to your destination equally undetected.
All participants will not only win a small snack, but also the chance to get a fully functional trial version of the Cybertrap Active Directory Deception solution until the end of the year. Just leave a short entry explaining why exactly your company would like to test Cybertrap. All winning hacker playground participants will also be entered into a draw at the end of the day to win one of the small-scale hacker games.

The current timetable Hall 7 – Booth 410
it-sa Exhibition Nuremberg, October 12-14, 2021
October 12th & 13th, 2021
9:00 | Opening CYBERTRAP Hacker Playground
10:00-10:15 | Endpoint Deception Demo
11:00-11:15 | Web Application Deception Demo
12:00-12:15 | Active Directory Deception Demo
12:30-13:30 | Exchange your feedback for a cool drink*
14:00-14:15 | Endpoint Deception Demo
15:00-15:15 | Web Application Deception Demo
16:00-16:15 | Active Directory Deception Demo
17:30-18:00 | Raffle Hacker Games
October 14th, 2021
9:00 | Opening CYBERTRAP Hacker Playground
10:00-10:15 | Endpoint Deception Demo
11:00-11:15 | Web Application Deception Demo
12:00-12:15 | Active Directory Deception Demo
12:30-13:30 | Exchange your feedback for a cool drink*
14:00-14:15 | Endpoint Deception Demo
15:00-15:15 | Web Application Deception Demo
16:00-16:15 | Active Directory Deception Demo
16:30-17:00 | Raffle Hacker Games
*while stocks last
Your free ticket for it-sa 2021
We will sponsor your tickets for Europe’s largest trade fair for IT security. Just fill out the form below for us to send it to you. Would you like more than one ticket? Then please contact our sales team or send us an email to sales@cybertrap.com.
What are the applications of Deception Technology?

Endpoint Deception
Even if endpoints are compromised, the corporate infrastructure remains protected.
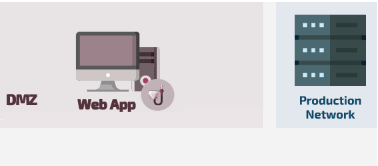
Web Application Deception
Used to strengthen security measures in the production network.
Active Directory Deception
Prevents attackers from hiding in the network from your security team’s tools.
Focus on it-sa 2021
Active Directory Deception
Active Directory (AD) is a standard tool used by most organizations to manage user and computer access to corporate resources. Therefore, every computer on the corporate network must have some level of access to AD in order for the network environment to function properly.
Attackers use phishing, man-in-the-middle and other techniques to gain the privileges they need to infiltrate a network. By gaining access to the Active Directory, attackers hope to hide from security teams and their tools by, for example, using existing credentials or creating their domains.
Cybertrap Active Directory Deception returns real-looking but false information to a hacker. As the attacker moves around the network, he is redirected to a secure Deception environment. This way he can be monitored every step of the way without causing any damage.
Have we piqued your interest?
Find more information in our blog:
“Never interrupt an enemy when he is making a mistake.”
– Napoleon Bonaparte



